-
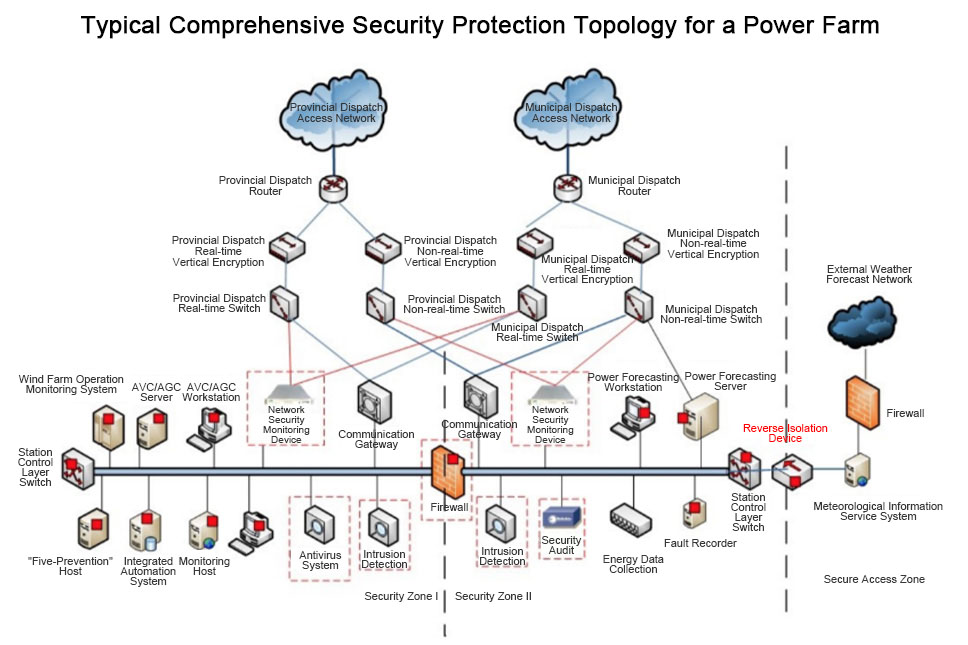
Intrusion Detection
Real-time monitoring of various data packets and network behaviors, providing timely alarm and response mechanisms
-
Security Audit
Audit the behaviors of monitoring systems and master station systems in the network, and perform operations such as querying, statistics, management, and maintenance based on stored records and operator permissions
-
Boundary Protection
Implement logical isolation to prohibit illegal connections and data
-
Virus Defense
Prevent virus intrusion into the system caused by improper use of mobile storage devices and laptops during equipment installation, debugging, or maintenance
-
Port Control
For uncontrolled exposed multi-type peripheral ports, implement effective peripheral port control through portable operation and maintenance gateways, USB security isolation, and host port control technologies.
-
Business Monitoring
Real-time monitoring of business modules such as AGC and AVC in two assessment criteria, identifying operational defects
-
Centralized Security Management
Achieve centralized monitoring, trusted protection, and secure operation and maintenance of network security for the centralized control center and its subordinate new energy stations
-
Advantage of Independent R&D
Independently developed security products enable us to better understand user needs